This article was published in “Xakep” #206 magazine, оriginal russian version - PDF
Zombie Scripting: Using BeEF for Advanced XSS Attacks
XSS attacks (cross-site scripting) have long since evolved beyond session hijacking through document.cookie to an attacker’s sniffer. Many might remember various online services that easily allowed the insertion of the necessary payload and waited for an email notification with the victim’s data. Now it’s 2016, so let’s leave all the above somewhere in 2007 and return to reality. Today, this article will discuss a popular tool that helps get the most out of a simple JS code injection. So, meet BeEF.
BeEF is a framework that allows centralized management of a pool of clients infected through XSS, issuing commands, and receiving results. It works as follows:
- The attacker injects the script
hook.jsinto a vulnerable site. hook.jssignals the C&C (BeEF) that a new client is online.- The attacker logs into the BeEF control panel and remotely “drives” the infected browsers: executes payloads and receives responses.
The victim only needs to run hook.js in their browser to become another “zombie” to which various commands can be sent, malicious executables can be injected, and so on. The attacker only needs to start beef-xss and open the control panel in a browser, where all the interesting things happen.
BeEF “out of the box” contains a myriad of built-in techniques, exploits, plugins, and significantly simplifies working with multiple clients simultaneously. Of course, the infected user may leave the page with the injected script, but for these cases, there is a Man-in-The-Browser attack, which allows tracking all client actions within the context of one domain, as long as they stay on the site or do not manually change the URL in the address bar.
Installing BeEF
To start, we need to install BeEF. I consider a scenario where we have our VPS/VDS somewhere in the cloud with a public IP address and Ubuntu 14.04:
1 | root@myownvpn:~# uname -a |
We follow the official instructions available in the GitHub repository. BeEF is written in Ruby, so the installation is standard for most small Ruby applications: rvm, ruby, bundler, and bundle install. There should be no issues.
By the way, BeEF is also included in the default Kali Linux 2 package, so if you are using Offsec’s creation, BeEF is already installed.
Usage
After launching beef-xss, open the link http://127.0.0.1:3000/ui/authentication in your browser and log in with beef:beef. Great, we have everything we need. To test BeEF, I suggest “hooking” your browser by going to /demos/basic.html. As seen in the source code, the very hook.js is loaded, and now in the Online Browsers section, a host and a list of “hooked” clients have appeared. These are our infected zombies.
If you select the desired client and go to the Commands tab, you will see a wide range of various techniques, exploits, attacks, and tricks that can be used with just a couple of clicks.
Social Engineering
To start with something simple and understandable, open the Social Engineering section and try phishing a Google account login. We need to specify the page to which the user will be redirected and the delay before the redirect. Fill in (or leave as is), click Execute, and magically, the page content changes to a familiar Google login interface!
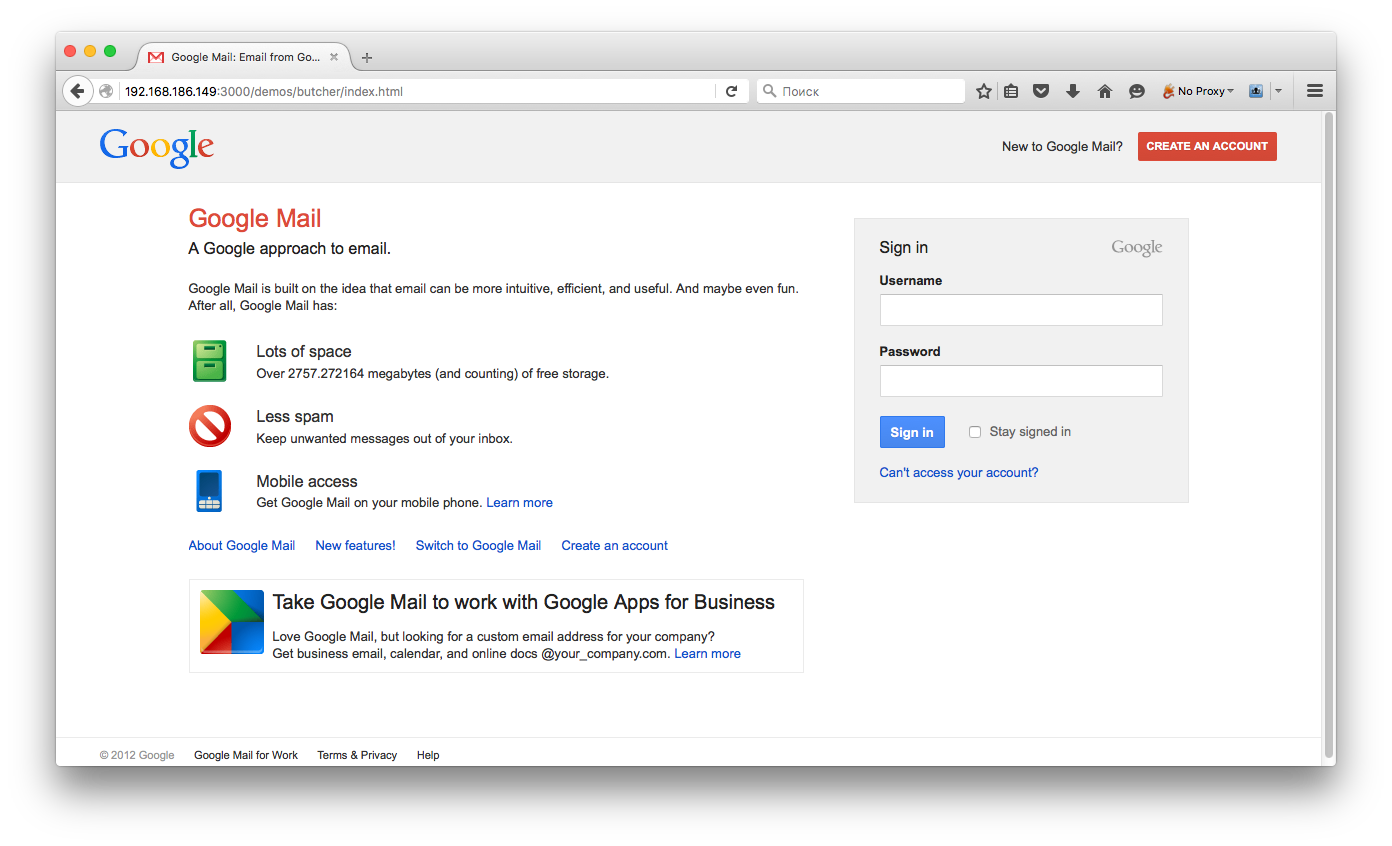
Let’s pretend to be the victim and enter some data. After clicking the Sign-in button, we are redirected to the actual Google login and the previously specified page. As seen in BeEF by clicking on the sent command, we successfully intercepted the user’s entered data.
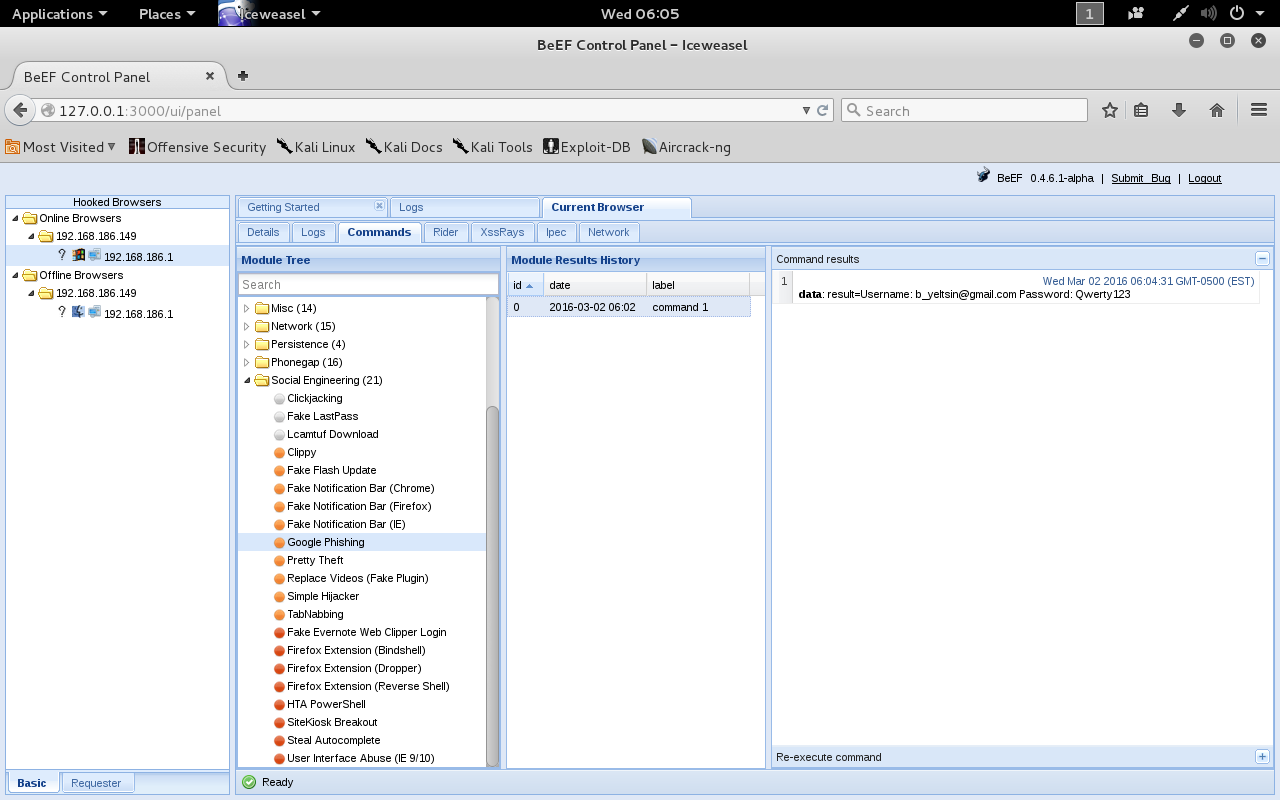
The Most Basic Commands
Where is the good old document.cookie that everyone needs? Right here, under Hooked Domain, there are enough commands for almost instant access to various information from the victim’s browser, including the coveted “cookies.”
This simple method allows getting a list of connected scripts and links on the page or the entire source code of the page. I advise paying special attention to a feature like link replacement—change everything so that every link on the page leads to the desired address. Among the available commands is even redirecting the user to a video of “Never gonna give you up”—classic, after all!
Fingerprinting
Besides all the above, there is a Browser section, where many useful features are gathered for maximum fingerprinting of the victim’s browser. You can find out the list of installed extensions in the browser, the presence of LastPass, FireBug, etc. Using the “Webcam” command, you can try to feed the user a Flash plugin to work with the webcam, although this technique is outdated, just like Flash itself. I won’t list and describe all the features but advise you to study them yourself while checking their relevance in modern browsers.
Exploits
The next interesting section is Exploits. Here you will find many ready-made vectors for exploiting various vulnerabilities. I recommend paying attention to exploits for different routers first. We have often written about how fatal bugs routers sometimes contain: harmless XSS can often escalate to full RCE through CSRF. This scenario repeats with many other devices in the potential victim’s network, be it NAS, cameras, local services, etc. The list of exploits may not boast zero-days or a vast selection, but no one forbids writing custom plugins for BeEF under your vulnerabilities!
Browser Attack, Sniffing Sent Data
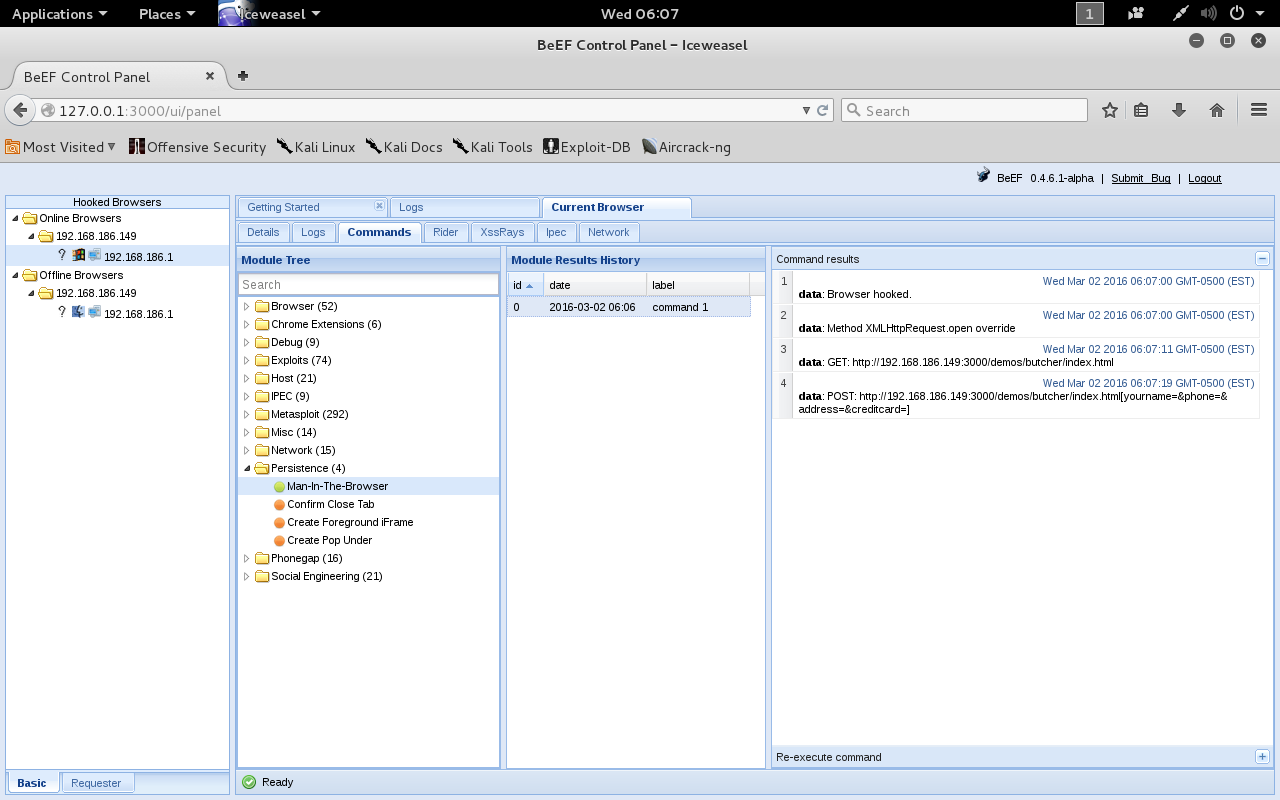
One of the most interesting attacks when using XSS is the Man-in-The-Browser attack. It allows tracking various actions of an infected user on the entire resource, not just the page with the payload. The effect is achieved by background loading the requested page on click and replacing the DOM without changing the actual browser location (similar to Rails’ turbolinks). Naturally, this feature works only under SOP: the requested page must have the same protocol, port, and domain; otherwise, the loading will not happen.
This feature is very convenient and can only be disabled by directly changing the URL address in the browser’s address bar. As seen in the logs, all actions performed by the user are displayed, such as entering and sending POST/GET requests, opening other sites in a new window, etc.
Network Work
Many functions from the Network section may not work; for example, social network detection stubbornly refused to work for me. I suspect that there used bugs/features that services have patched. But don’t be upset: always remember that sometimes even one XSS in the victim’s browser can lead to the compromise of the entire home network. Therefore, pay attention to various network scanners presented in BeEF. As practice shows, not all of them will work in modern browsers, but the GET HTTP servers command worked for me and honestly found an old Zyxel with a web interface in the local network. Of course, server detection is straightforward and is based on trying to load favicon from each specified IP range.
Also, I recommend looking at a remarkable feature like network scanning using a DNS name dictionary. Who knows, maybe you named your router “router” for convenience?
MSF
Detecting and fingerprinting the internal network is, of course, great, as well as trying to use various exploits for routers with various CSRF/XSS/etc. But what if we want to be cool hackers and try to break the victim’s browser right away? Nothing could be easier, as BeEF supports using Metasploit. These are not private bundles with 0day, but no one guarantees that the user will have the latest version of the browser/plugins!
To pair Metasploit and BeEF, you need to do a few simple steps:
Open the main
config.yaml(in Kali, it was located at/usr/share/beef-xss/), find theExtensionsection, and change theenableparameter totruein Metasploit.Open the Metasploit plugin settings file (e.g.,
/usr/share/beef-xss/extensions/metasploit/config.yaml) and change thehost,callback_hostparameters (the rest at your discretion).Launch Metasploit and execute the command:
1
msf > load msgrpc ServerHost=192.168.186.149 User=msf Pass=abc123
Restart BeEF, and you will see several hundred Metasploit modules available for use. Let’s look at a simple example of using the BeEF + Metasploit bundle. We will take the browser_autopwn2 module, configure it, and run it.
1 | msf > use auxiliary/server/browser_autopwn2 |
For ease of use and setup, I specified /autopwn as
URIPATH. Now go to BeEF, select the Misc section, and use the command to add an invisible frame. In the address field, specify something like http://our_ip:8080/autopwn. After sending the command, you can see that the frame with the bundle loaded in the victim’s browser, and the rest is up to Metasploit. Similarly, you can use other Metasploit and SET modules (an excellent tool with a wide range of possibilities for social engineering attacks).
Browser Extension Attacks
Another interesting and frequently used attack vector is attacking the user’s extensions. If successful, it guarantees us much more capabilities than a simple script injection on a website, as extensions have much more rights. For these purposes, an analogue of BeEF was created, which eventually grew into an independent framework — Chrome Extension Exploitation Framework, or simply ChEF. Its features include:
- Monitoring open tabs in the browser.
- Global execution of JS code on any tab (global XSS).
- Reading http-only cookies.
- Retrieving and modifying browser history.
- Taking screenshots of browser windows.
- Accessing the file system through file://.
- Injecting BeEF.
This tool is worth mentioning, but it deserves a separate article, so we will not describe all that ChEF is capable of in this article.
Conclusions
Of course, more BeEF functionality could be described, such as phonegap, infecting mobile applications, usage during MiTM, etc., but all this unfortunately does not fit into one article. In short, BeEF is indeed the most convenient and coolest (in all senses) framework for working with XSS, squeezing the absolute maximum out of a simple JS code injection, leaving room for creativity (BeEF is an open-source project), and supporting custom plugins. This tool is perfectly suited for conducting pentests, solving various CTF tasks, and everything else your imagination can come up with.